Is your VPN Secure?
What is VPN and how does it work?
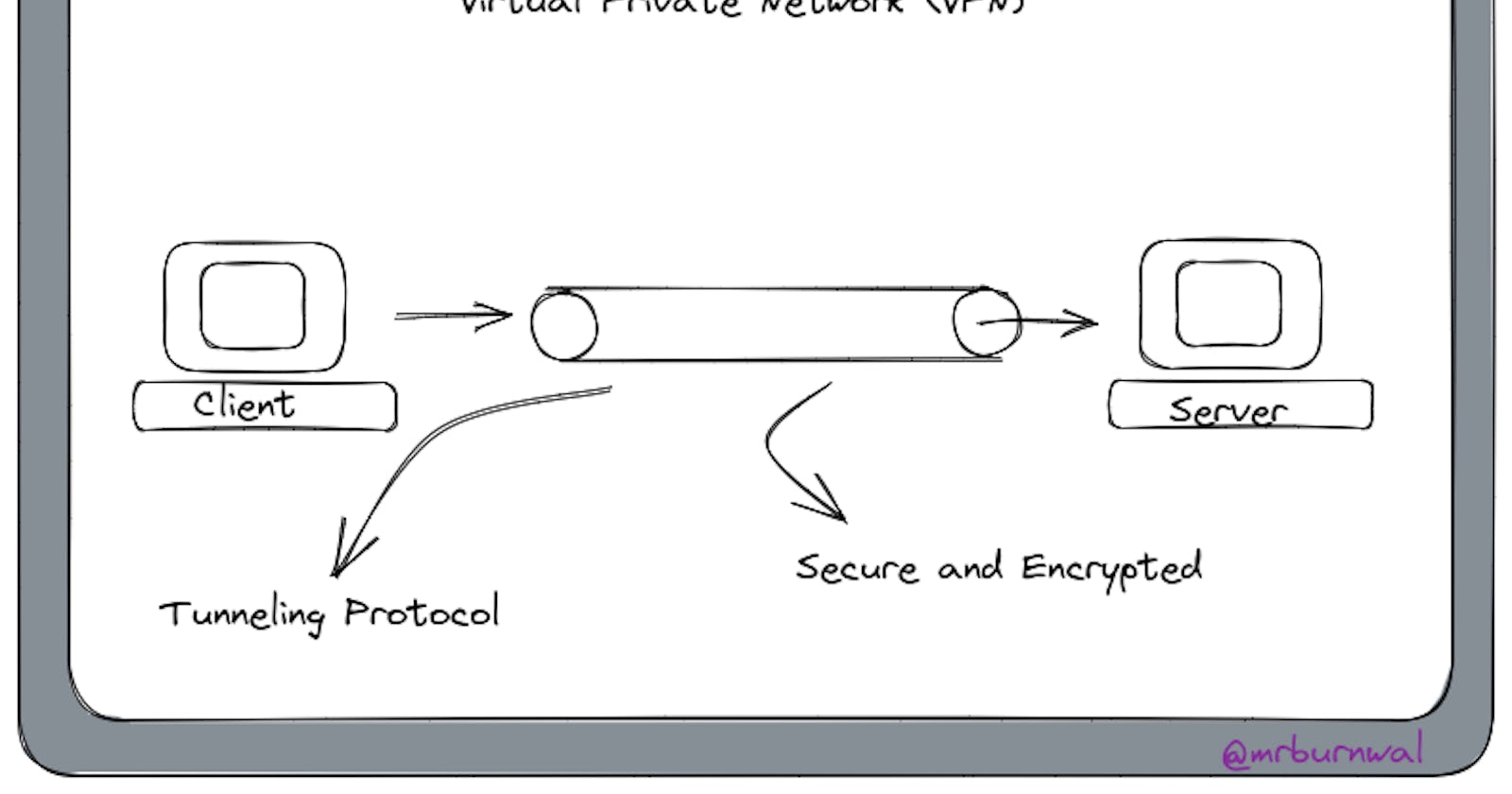
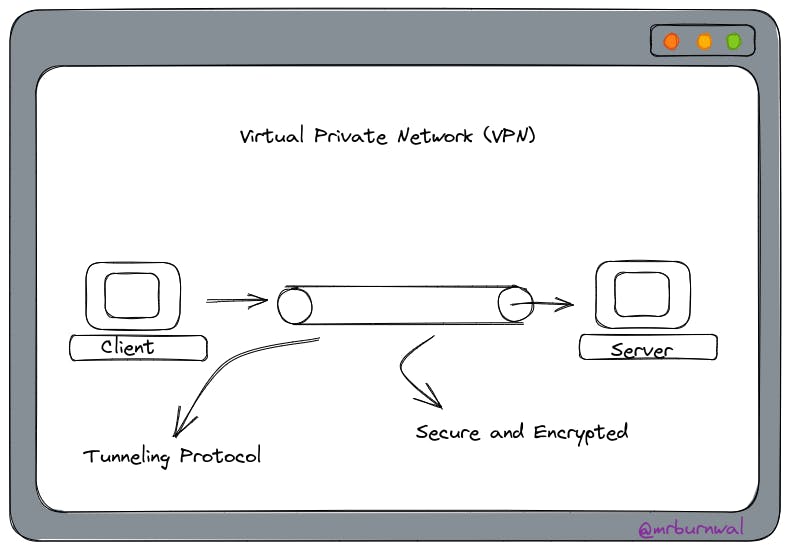
In general terms, VPN is something that provides Privacy, Security, Anonymity and Access to blocked content over the internet. VPN stands for Virtual Private Network and allows computers to think that they are on the same network.
In order to provide a secure connection, VPN uses a tunnelling protocol that ensures that the data is only readable by the intended recipients and cannot be intercepted by unauthorized parties. VPNs use encryption to secure data transmission and protect it from man-in-the-middle attacks.
What is tunnelling protocol?
A tunnelling protocol in VPN is a method used to add an extra layer of security to a connection. It allows for data to be transmitted securely over a public network by encapsulating it in a "tunnel" that is protected by encryption.
What happens if VPN suspects a man-in-the-middle attack?
If a VPN suspects a man-in-the-middle (MitM) attack, it will typically disconnect the session and notify the user. This occurs due to several reasons:
Authentication Failure
Encryption Failure
Certification Failure
Sudden loss of packets.
VPN application that we use on phones, How does that work?
When you use a VPN application on your phone, the app establishes a secure connection between your phone and a remote server. The app acts as a client, and the remote server acts as the VPN server.
Once the connection is established, all of your internet traffic is routed through the VPN server, which acts as a middleman between your phone and the internet. This allows the VPN to hide your real IP address, making it appear as if you are located in a different location. Additionally, the VPN encrypts your internet traffic, making it difficult for anyone to spy on your online activities.
Does Tor Browser work as VPN?
The Tor Browser is based on the Tor network, which is similar to a VPN in that it provides a secure and anonymous way to access the internet. When you use the Tor Browser, your internet traffic is encrypted and routed through multiple randomly-selected nodes on the Tor network. Each node only knows the location of the previous and next node in the circuit, and your IP address is hidden from all of them. This makes it very difficult for anyone to track your online activities or determine your location.
Summary
VPN works on server-client architecture and tunnelling protocol that provides secure connection where data transmission is encrypted between point-to-point nodes. Whereas Tor browser uses a layered approach called "onion routing" and it aims to provide anonymity and not just privacy.